Banka Ekonomike is a fully owned local capital bank operating in Kosovo since it was licensed in 2001. It currently employs 300 to 400 employees and has more than 30 branches across the country. Unfortunately, the bank suffered a data breach on 19th of April 2020, which became a headline in local news five days later. We had enough time to excavate the data dump and provide detailed insights for this particular cybersecurity incident.

Ransomware is a common form of malware designed to deny access to critical data and systems, typically through encryption, until a sum of money has been paid by the compromised party. During the end of February 2020 there was an indication that Banka Ekonomike (BEK) had allegedly fallen victim to such a cyber-attack. However, there was no further update in that regard up until April 23 when a ZDNet reporter denoted BEK in a breach incident which involved more companies as seen in the following Twitter thread:
A - AFPA
— Catalin Cimpanu (@campuscodi) April 23, 2020
C - Container Marketing, Inc
B - Boom Construction Company
B - Banka Ekonomike
C - City of Torrance, CA
D - D'Asign Source
C - Chris-Marine
What do I win?
Apparently, a well-known group behind the attack posted a tweet of company initials which they had compromised and were releasing the exfiltrated data in response for them not paying the ransom within the deadline. Catalin’s status update was seen in the morning of the other day, which gained attention from local news media and portals within hours. There were various news versions that day which included inaccurate information. At first, some believed that the data dump is for sale in the dark web (‘black market’); for maximum reputational damage, ransomware authors made sure that the data dump is accessible in the public web which everyone can access, and without any payment at all – everything can be downloaded for free.
Since then, the Information and Privacy Agency (IPA), an independent agency in charge of supervising the implementation of data protection rules and access to public documents in accordance with the applicable law, has not yet made any public statement. On the other hand, the Central Bank of Kosovo (CBK) released a statement on April 24 ensuring that clients’ financial assets are safe and unaffected – which implies that online transactions are blocked.
DoppelPaymer, as initially seen in the picture attached to the reporter’s tweet, is a ransomware family which shares most of its code with a previous infamous ransomware—BitPaymer—operated by INDRIK SPIDER – a threat group believed to originate from Russia. However, there are a number of differences between DoppelPaymer and BitPaymer, which may signify that some members may have split from the original threat group and forked the source code of Dridex, a famous banking trojan, and BitPaymer to start their own operation.
They target big entities of specific industries such as banking and healthcare, and usually demand payments ranging from 40 to 100 Bitcoins (translates to a range of circa 320,000€ to 800,000€ at the time of writing this article); more technical information with reference to the campaign can be found in 2-Spyware. Moreover, on top of encrypting IT assets, actors behind this ransomware also ensure a copy of the compromised data which is then leaked online in their dedicated website(s) if their demands are not met. This is a tactic that researchers call “double extortion” – which is what happened to BEK along 11 other entities whose data was leaked during the month of April.
Leaked data, when uncompressed, produced around 71GB worth of mainly financial and client information. We have divided our results in three categories with their key exposed attributes:
Here is a screenshot of a small fraction of data:
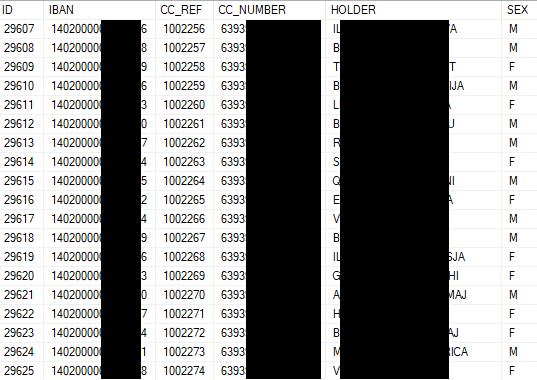
End of day reports make up 93% of total breached data volume.
There are two crucial points when it comes Kosovo’s Law On Protection Of Personal Data (No. 06/L-082).
According to article 33, in case of a personal data breach event, the data controller has a window of seventy-two (72) hours available to notify the IPA (formerly known as the National Agency for the Protection of Personal Data) after being informed about the incident. CBK stated that BEK has notified relevant authorities in charge of Cyber Security and Data Protection that day.
Article 105 provides details with regard to financial penalties for cases of serious and great violations of legal provisions. It states that the Agency may impose a fine ranging from 20,000€ to 40,000€ or in the case of a company/enterprise 2% to 4% of annual turnover of the preceding fiscal year in compliance with the Regulation (EU) 2016/679 of the European Parliament.
Ransomware targets home users, businesses/enterprises, as well as government networks and can lead to loss of sensitive or proprietary information, disruption of day-to-day operations, financial losses incurred to restore systems and files, and considerable reputational damage.
While the vector of attack for BEK is yet unclear, threat actors tend to use targeted malicious emails or outdated computer system vulnerabilities. To avoid such scenarios, we have compiled a comprehensive list of preventive measures that users and administrators should consider to protect their computer networks based on industry best practices and mitigation strategies:
Furthermore, a Business Continuity Plan (BCP) is critical to ensure proper functioning of key services in case of a disruption (cybersecurity attacks or even natural disasters) by leveraging the Disaster Recovery Center (DRC).
